As described on the following.
https://www.crc.id.au/linux-and-usb-full-disk-encryption/
Flow
# mkdir /etc/luks-keys
# chmod 700 /etc/luks-keys
# dd if=/dev/urandom of=/etc/luks-keys/new-key-file bs=1 count=4096
# cryptsetup luksFormat /dev/sdb /etc/luks-keys/new-key-file
# cryptsetup luksUUID /dev/sdb
# mv /etc/luks-keys/new-key-file /etc/luks-keys/48a05e5e-1338-4278-a5cb-69657b2423e4
# chmod 400 /etc/luks-keys/48a05e5e-1338-4278-a5cb-69657b2423e4
# cryptsetup –key-file /etc/luks-keys/48a05e5e-1338-4278-a5cb-9657b2423e4 open /dev/sdb luks-48a05e5e-1338-4278-a5cb-69657b2423e4
# mkfs.ext4 /dev/mapper/luks-48a05e5e-1338-4278-a5cb-69657b2423e4
# mount /dev/mapper/luks-48a05e5e-1338-4278-a5cb-69657b2423e4 /mnt/luks/
# umount /mnt/luks
# cryptsetup close luks-48a05e5e-1338-4278-a5cb-69657b2423e4
# mount /dev/mapper/luks-48a05e5e-1338-4278-a5cb-69657b2423e4 /mnt/luks/
# umount /mnt/luks
# cryptsetup close luks-48a05e5e-1338-4278-a5cb-69657b2423e4
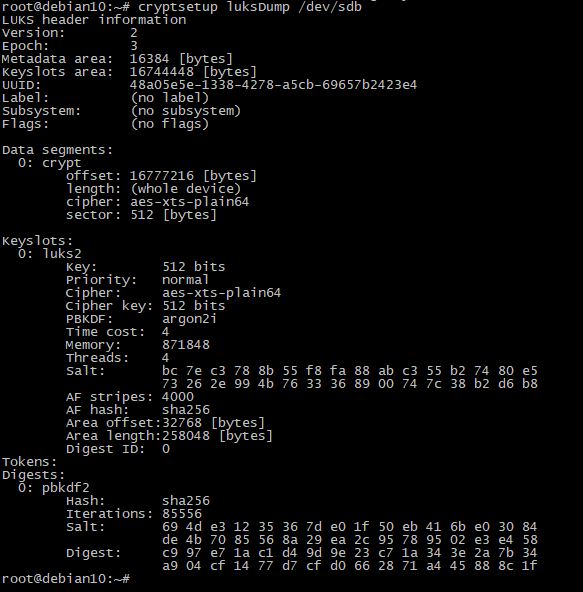
LuksDump
# cryptsetup luksDump /dev/sdb
LuksFormat options
cryptsetup -v –cipher aes-xts-plain64 –key-size 512 –hash sha512 –iter-time 2000 –use-random –verify-passphrase luksFormat /dev/sdb
Displaying status
# cryptsetup status luks-48a05e5e-1338-4278-a5cb-69657b2423e4
/dev/mapper/luks-48a05e5e-1338-4278-a5cb-69657b2423e4 is active.
type: LUKS2
cipher: aes-xts-plain64
keysize: 512 bits
key location: keyring
device: /dev/sdb
sector size: 512
offset: 32768 sectors
size: 41910272 sectors
mode: read/write
TODO:
Pull certificate from Yubikey PIV Smartcard